Water Utility Cybersecurity and Resilience: Protecting Assets

Kristian Storm
Co-Founder & CEOIntroduction
Water utilities are the backbone of modern society, ensuring clean and safe water delivery to millions. However, with the rapid adoption of digital technologies like IoT sensors, SCADA systems, and remote monitoring, water utility cybersecurity is now a critical priority.
For Waltero, Securing digital water infrastructure is no longer optional, it’s essential.
This article explores the cybersecurity challenges facing modern water utilities, the vulnerabilities that expose them to attacks, and best practices to enhance critical infrastructure security. We’ll also share real-world lessons and strategies that can help water providers build network resilience and safeguard their digital assets.
The Rising Threat Landscape: Why Cybersecurity is Mission-Critical
Cyber threats against water infrastructure have escalated, targeting everything from smart meters and edge devices to industrial control systems (ICS) that manage treatment and distribution. These cyber attacks pose significant threats to public health and infrastructure, leading to severe operational disruptions and substantial financial costs, particularly for smaller utilities that may lack robust cybersecurity measures.
The water industry isn’t immune to hacks, recent years have seen high-profile incidents, such as:
Remote access exploits: In one alarming case, hackers gained entry to a U.S. water treatment plant’s remote control system and attempted to alter chemical levels in drinking water systems.
Ransomware attacks: A major UK water provider was hit with ransomware that disrupted IT systems, underscoring the vulnerability of water SCADA security.
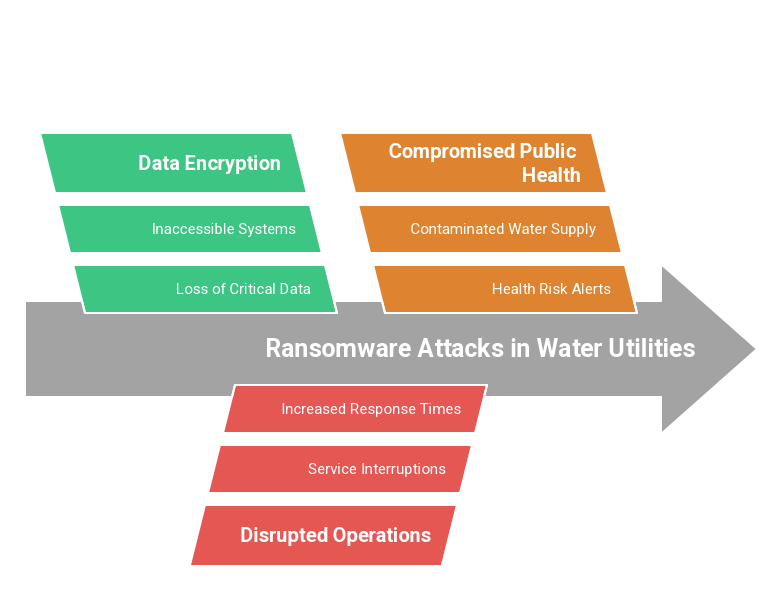
IoT device breaches: Smart meters, pumps, and edge sensors have been compromised due to weak authentication and outdated firmware, allowing attackers to manipulate water distribution remotely.
Waltero’s Solution For Water Utility Cybersecurity
Cybersecurity is crucial for the water sector and wastewater systems, with various initiatives and resources available to improve resilience against cyber attacks. Registration requirements, federal funding opportunities, and uniform cybersecurity standards are necessary to protect these critical infrastructure sectors.
The Environmental Protection Agency (EPA) has been instrumental in providing cybersecurity resources and protocols to help safeguard these systems.
Why are water system cyber threats happening?
Legacy Systems: Many water plants still use outdated industrial control systems (ICS) with little to no built-in security.
IoT Expansion: More devices mean a larger attack surface, especially when default credentials and weak encryption are in play.
IT/OT Convergence: The blending of corporate IT networks with operational technology (OT) introduces new security gaps.
Limited Cyber Resources: Many utilities lack dedicated cybersecurity teams or real-time threat monitoring capabilities.
How can you prevent your utility or business from such cyber incidents?
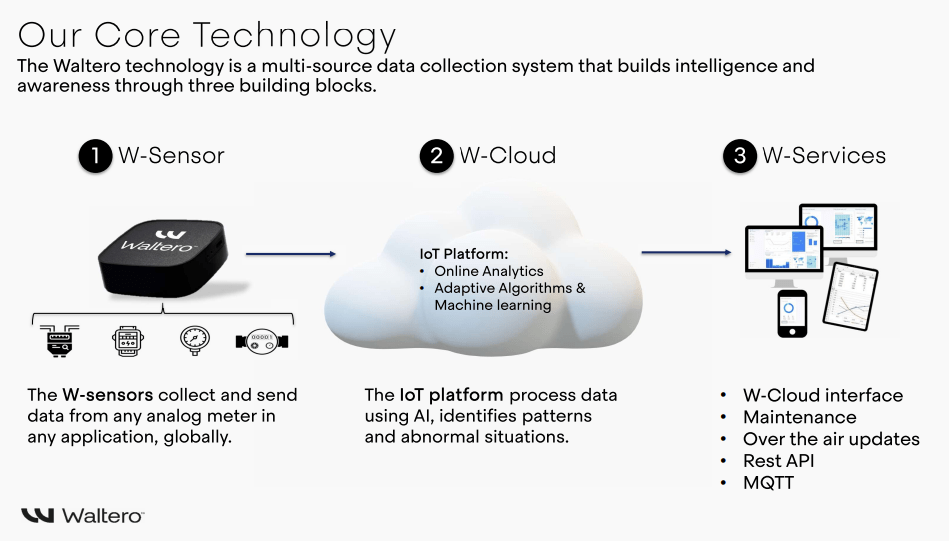
This is where Waltero’s Waltero helps safeguard your utility or business from cyber incidents by integrating intelligent, edge-based security solutions that minimize vulnerabilities and enhance real-time threat detection. By leveraging our deployable Edge AI technology, we reduce reliance on centralized cloud systems, limiting exposure to cyber threats while ensuring secure data processing at the source of the W-Cloud.
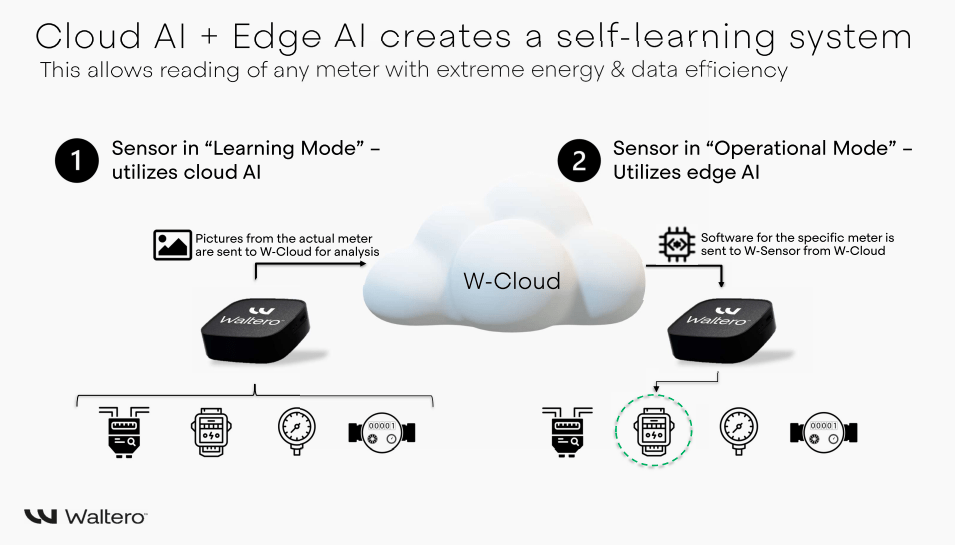
Our W-Solution incorporates an end-to-end encryption system and communication, continuous monitoring, and automated anomaly detection to proactively identify and mitigate risks before they escalate.
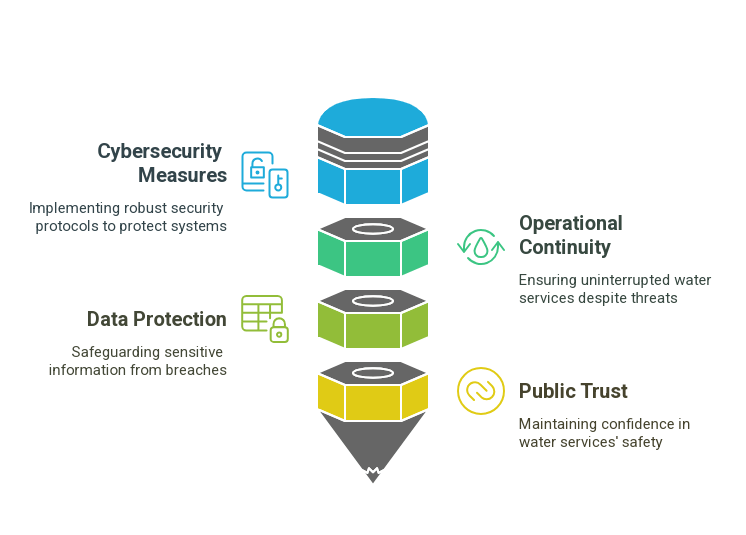
With Waltero’s expertise in IoT security and resource intelligence, you can strengthen your cybersecurity framework, protect critical infrastructure, and maintain operational resilience in an increasingly digital world.
Without a proactive cybersecurity strategy, these vulnerabilities can be exploited, leading to service disruptions, data breaches, or even contamination of public water supplies.
Key Cybersecurity Challenges in Digital Water and Wastewater Utilities
1. Securing Edge & IoT Devices
The rise of IoT device security in water and wastewater systems brings efficiency but also introduces security gaps. Unsecured smart meters, pressure sensors, and remote terminal units (RTUs) can be exploited if they lack:
Strong authentication (default or weak passwords are common).
End-to-end encryption (data in transit is often unprotected).
Regular firmware updates (many IoT devices remain vulnerable for years).
As a Solution, Water utilities should enforce device-level encryption, multi-factor authentication (MFA), and automated firmware updates to prevent unauthorized access.
2. SCADA and OT Network Vulnerabilities
Water SCADA security is a top concern, as these systems control critical treatment and distribution processes. Many SCADA networks are outdated and use flat architectures, allowing attackers to move laterally once inside.
The Cybersecurity and Infrastructure Security Agency (CISA) plays a crucial role in promoting cybersecurity measures for SCADA and OT networks.
Solution: Implement network segmentation, isolating OT networks from IT systems and limiting cross-network traffic. Deploy intrusion detection systems (IDS) and firewalls tailored for industrial environments.
3. Ransomware & Insider Threats
Ransomware attacks on water utilities and the wastewater sector can cripple billing systems, SCADA workstations, and emergency response capabilities. In some cases, insiders—whether disgruntled employees or negligent contractors—have caused serious breaches.
Solution: Regular data backups, air-gapped storage, least-privilege access policies, and cybersecurity training can mitigate these risks.
4. Lack of Real-Time Monitoring & Incident Response
Most utilities don’t have continuous monitoring of their operational networks, making it difficult to detect cyber intrusions before they cause damage. This is especially critical for wastewater systems, where real-time monitoring and incident response are essential to ensure the safety and reliability of water services.
Solution: Deploy AI-driven anomaly detection, security operations centers (SOCs), and automated threat response tools. Scheduled network monitoring ensures early detection of suspicious activity.
Best Practices for Enhancing Cyber Resilience
To counteract these digital water utility risks, we must implement a multi-layered cybersecurity strategy. Here’s how:
Proactive information sharing and reporting of cyber incidents within the water and wastewater sector are crucial to protect infrastructure and enhance cybersecurity measures.
1. Strengthen Access Controls & Authentication
Strengthening access controls & authentication is a priority against cyber risks, we can achieve so through:
Enforce multi-factor authentication (MFA) for SCADA and remote logins to strengthen access controls for water and wastewater utilities.
Disable default credentials on IoT and industrial devices.
Limit administrator privileges and regularly audit access logs.
2. Implement Network Segmentation & Firewalls
The implementation of network segmentation & firewalls can be realized by:
Separate IT and OT networks with firewalls and secure gateways.
Use micro-segmentation to limit access between different control zones.
Monitor east-west traffic to detect unauthorized lateral movement.
3. Secure Edge & IoT Devices
When securing edge & IoT devices, we can protect it through:
Encrypt data communications between field sensors and control centers.
Regularly update device firmware and patch vulnerabilities.
Require zero-trust authentication for any external access.
4. Enhance Ransomware Defenses
The water sector can work on enhancing ransomware defences by:
Conduct regular, air-gapped backups of SCADA configurations.
Deploy endpoint detection & response (EDR) tools to flag early-stage ransomware activity.
Train employees to recognize phishing and social engineering attacks.
5. Improve Incident Response & Continuity Planning
Incident response and continuity planning should always be in an improvement phase so that water utilities can have a proactive process in case of any cyber threats occurring.
Develop fail-safe contingency plans to maintain operations during cyber incidents.
Establish backup communication channels, such as radio or satellite links.
Run tabletop exercises to simulate cyberattack scenarios and refine response strategies.
Compliance & Industry Standards
Regulators worldwide are tightening cybersecurity requirements for water utilities. Key frameworks include:
ISA/IEC 62443: Security standards for industrial control systems.
NIST Cybersecurity Framework (CSF): Best practices for risk assessment and resilience.
EU NIS2 Directive: Mandates cybersecurity risk management for water providers.
EPA Cybersecurity Assessments (USA): Increasing oversight of public water system security.
Wastewater utilities also play a crucial role in adhering to cybersecurity standards and regulations, ensuring the resilience of these essential services against various cyber risks.
By aligning with these standards, utilities can strengthen security postures, reduce regulatory risks, and improve incident response capabilities.
Real-World Lessons: Water Utilities Responding to Cyber Threats
South Staffordshire Water Ransomware Attack (UK, 2022)
Attackers breached IT systems but failed to disrupt water supply due to strong network segmentation and response planning.
Lesson: Separating IT from SCADA networks can prevent operational downtime.
Florida Water Plant Cyber Intrusion (USA, 2021)
Hackers gained remote access and attempted to alter chemical dosing.
The attack was stopped by an alert operator and built-in fail-safes.
Lesson: Restricting remote access and enforcing MFA could have prevented this breach.
Conclusion
As digital transformation accelerates, water utilities must adopt a security-first mindset. At Waltero, we believe that with the right technologies, policies, and training, utilities can outpace cyber threats and maintain resilient operations.
We, at Waltero, encourage utilities to explore innovative cybersecurity solutions tailored for water infrastructure. If you’re looking for ways to assess and enhance your security posture, check out Waltero’s Exploratory Kit for insights on next-generation water cybersecurity strategies.
%3Aformat(webp)&w=3840&q=75)



